WiFi Signal Metrics: Key KPIs for Networks
Compare RSSI, SNR and signal loss to diagnose WiFi issues, optimize access point placement, and reduce interference for stable voice, video, and data.
Learn phishing methods, red flags, how to verify senders and links, avoid malicious attachments, report scams, and protect your accounts.
Phishing scams trick you into sharing sensitive information like passwords or credit card details. Cybercriminals often pretend to be trusted sources - banks, colleagues, or even friends - to deceive you. These scams are becoming harder to detect as attackers use advanced tactics, including fake emails, texts, and phone calls. Here's what you need to know:
Phishing is evolving, but staying cautious and verifying messages can protect your data. Learn how to identify and avoid these scams below.
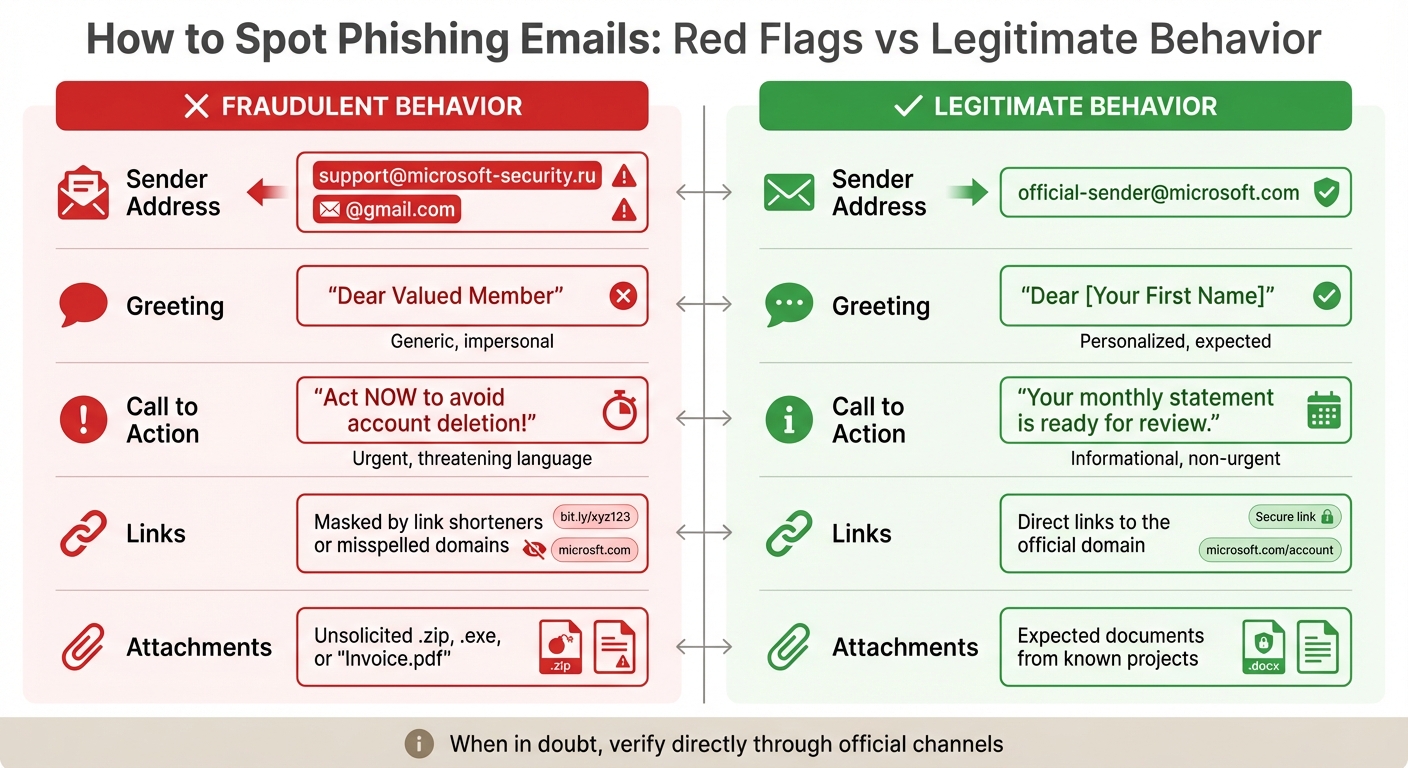
Phishing Email Red Flags: Fraudulent vs Legitimate Behavior Comparison
Spotting phishing attempts starts with carefully examining the sender. Scammers often use familiar names to trick you into acting quickly. But that friendly name might be a disguise - checking the actual email address can reveal the fraud.
Take a moment to hover over the sender's name (or long-press on mobile) to see the full email address. For instance, if "Microsoft Support" emails you from "support@gmail.com" or "paypal-security@secure.ru", it’s likely a scam.
Legitimate businesses use official domains, not free email services like @gmail.com, @yahoo.com, or @hotmail.com. Microsoft highlights this issue, warning that emails claiming to be from reputable companies but sent from domains like Gmail.com or microsoftsupport.ru are likely fraudulent. Also, pay attention to domain extensions. A U.S. bank using a Russian (.ru) or Brazilian (.br) domain is a major red flag.
Another tactic scammers use is typosquatting - registering domains with subtle errors or substitutions. For example, "micros0ft.com" replaces the letter "o" with a zero, while "rnicrosoft.com" uses "r" and "n" to mimic the letter "m." The University of Chicago has issued warnings about phishing attempts using addresses like "sender@uchicago.com" or "sender@maildrop.cc" instead of the legitimate "sender@uchicago.edu." In one notable case, Webroot uncovered a fake Charles Schwab email where hovering over links revealed a spoofed destination.
Don’t forget to check the "To" field. Legitimate emails are usually addressed specifically to you. If you see "undisclosed-recipients" or a long list of unknown addresses, it’s likely a mass phishing attempt.
After verifying the email address, take a closer look at the sender’s behavior for more clues.
Even if the email address seems legitimate, pay attention to the tone and details of the message. A mismatch between the display name and the email address - like "John Smith from IT" using "no-reply@randomsite.com" - is a clear warning sign. Scammers often use urgent or threatening language, such as "Act NOW to avoid account deletion!" or "Your account will be suspended within 24 hours", to pressure you into acting without thinking.
Generic greetings are another red flag. Messages starting with "Dear Valued Customer", "Dear Sir or Madam", or "Dear Member" instead of your name are often fraudulent. According to the University of Chicago Information Security team, legitimate organizations you have dealings with will typically address you personally. Also, watch for unusual tones or awkward phrasing, like a colleague suddenly being overly formal or an organization using repetitive, robotic language.
Be particularly cautious if the email includes unexpected attachments or links, such as a "shipping notification" for a package you didn’t order or an "urgent invoice" from an unfamiliar vendor. Always verify such messages using a separate channel, like calling the sender directly or visiting their official website. Never rely on contact details provided in the suspicious email. Many email clients, such as Outlook, now display security banners, flagging messages they "could not verify the sender" or marking them as [External] - both of which should prompt extra caution.
| Red Flag | Fraudulent Behavior | Legitimate Behavior |
|---|---|---|
| Sender Address | support@microsoft-security.ru or @gmail.com | official-sender@microsoft.com |
| Greeting | "Dear Valued Member" | "Dear [Your First Name]" |
| Call to Action | "Act NOW to avoid account deletion!" | "Your monthly statement is ready for review." |
| Links | Masked by link shorteners or misspelled domains | Direct links to the official domain |
| Attachments | Unsolicited .zip, .exe, or "Invoice.pdf" | Expected documents from known projects |
After confirming the sender's identity, the next step is to carefully examine any links or attachments in the email. Scammers often rely on people clicking without thinking, so taking a moment to inspect these elements can save you from malware, ransomware, or having your credentials stolen. Let’s break down how to handle links and attachments effectively.
Take a close look at links before clicking. Hover your mouse over the link to preview the URL, and focus on the root domain (the part between the second-to-last dot and the first slash) to determine if it's legitimate. If you're on a mobile device, long-press the link to reveal its URL.
Here’s an example: in the URL "microsoft.login.com.scam.co/login", the actual domain is "scam.co", not Microsoft. Digital Check Corp. explains:
"The root domain name – what comes after the second-to-last dot but before the first slash – is the only part of a website's address that scammers can't change".
Be cautious if you see hyphenated domains pretending to be major companies, like "one-note.com" instead of the real "onenote.com". Also, confirm that the domain extension aligns with the organization's location.
For extra security, copy the link and run it through a reputation checker like NordVPN Link Checker, URLVoid, or Norton Genie to scan for malware without visiting the site. If you use a password manager, it can also help by refusing to auto-fill credentials when the domain doesn’t perfectly match the legitimate site. When in doubt, skip the link entirely and type the official website address directly into your browser.
Once you’ve ensured the links are safe, turn your attention to any attachments.
Attachments from unknown or unexpected sources are often a red flag. They could contain malware, so it’s best to confirm directly with the sender using a separate, trusted communication channel. Before opening any file, scan it with reliable antivirus software.
Pay extra attention to file types like PDFs, Microsoft Office documents (Word or Excel), and executable files (.exe or .bash). Office documents are particularly risky if they ask you to "Enable Macros", as this can activate malicious code. Never respond directly to the suspicious email - scammers usually control that address.
If something about the email doesn’t feel right, trust your instincts. Use the "Report Phishing" or "Report Junk" feature in your email client to alert your provider, and then delete the message. Mozilla Infosec emphasizes:
"Your own intuition is probably your best asset for easily detecting phishing attacks. If an email seems out of place, unsolicited or asks you to take a weird action, stop and consider whether you are in a phishing scenario".
Once you've checked the technical details of an email, it's time to dig into the content itself. The way an email is written can often reveal whether it's legitimate or a phishing attempt.
Phishing emails are infamous for using language designed to create panic or urgency, pushing you to act without thinking. As Microsoft Support explains:
"Creating a false sense of urgency is a common trick of phishing attacks and scams. They do that so that you won't think about it too much or consult with a trusted advisor who may warn you".
Be on the lookout for messages claiming your account will be deactivated, threats of legal action like arrest warrants, or even claims of an IRS investigation. Financial scare tactics are also common, such as fake invoices demanding "Payment Due Immediately" or alerts about issues with your payment details. If an email makes you feel pressured or uneasy, take a step back. Instead of clicking on links, verify the claim by logging into the official website directly.
Legitimate companies usually address you by your name. Phishing emails, on the other hand, often use generic greetings like "Dear Customer", "Dear User", or "Dear Valued Member" to cast a wide net. A lack of personalization is a red flag. Be especially cautious if an email calls you by your email address instead of your actual name.
Professional organizations take their communications seriously, employing skilled writers and editors to ensure quality. Obvious grammar mistakes or awkward wording can be a strong indicator of phishing. As the Better Business Bureau points out:
"Legitimate companies have their email messages written by professionals, edited and revised so they never come across as unprofessional".
Pay attention to odd phrases, inconsistent tone, or glaring errors like "Your account has been temporary suspend." Also, double-check the sender's domain for subtle misspellings, such as "help@microsft.support" instead of the official address. Reading the email aloud can help you catch awkward phrasing that might otherwise slip by. Legitimate emails are polished and professional - anything less should raise your suspicion.
If you think you've encountered a phishing attempt, here's what you should do next.
Stop immediately - don’t click on any links, open attachments, or respond to the email. Microsoft offers this important advice:
"Whenever you see a message calling for immediate action take a moment, pause, and look carefully at the message. Are you sure it's real? Slow down and be safe."
Instead of using any contact details provided in the suspicious message, rely on trusted sources. For instance, use a phone number from a previous bill or manually enter the official website URL into your browser. Another option is to check the organization’s official mobile app to see if there’s any legitimate issue with your account.
Reporting phishing attempts can help stop scammers in their tracks. Forward suspicious emails to reportphishing@apwg.org and report them to the FTC at ReportFraud.ftc.gov. If you receive a phishing text, forward it to SPAM (7726). For messages targeting work or school accounts, inform your IT support team as soon as possible.
Once you’ve reported the scam, focus on securing your digital information.
If you’ve interacted with a suspicious message, take action right away. Change your passwords to strong, unique ones, enable multi-factor authentication, and run a full antivirus scan. If you’ve shared sensitive details, visit IdentityTheft.gov for guidance. The Information Security Office at UC Berkeley reminds us:
"The first rule to remember is to never give out any personal information in an email."
Acting quickly can help limit the damage and protect your accounts from further harm.
Phishing scams thrive on urgency and emotional triggers, pushing people to act without thinking. The best way to protect yourself is to slow down and take a moment to assess any suspicious message before reacting.
Check sender addresses for slight misspellings, hover over links to see where they actually lead, and watch out for red flags like urgent wording, vague greetings, or requests for private details. Legitimate companies won’t ask for your passwords, Social Security numbers, or banking info via email or text. If something feels off, reach out to the organization directly using contact details from their official website or a trusted source - not the ones in the questionable message. Also, enabling multi-factor authentication and keeping your devices updated automatically can add an extra layer of security.
These simple steps can go a long way in safeguarding your digital life. And if you’re looking for professional help, keep reading to learn how TekDash can assist.
TekDash offers both on-site and remote support to help secure your digital world. Their team can set up multi-factor authentication, manage security software updates, resolve network issues, and even handle smart home device installations. With their expertise, you can go about your day with confidence, knowing your online security is in good hands.
Spotting a phishing email is all about staying alert and paying attention to the details. Start by examining the sender's email address. Legitimate organizations stick to official domains, so if you notice misspellings or strange, unfamiliar domains, consider it a red flag. Before clicking any links, hover over them to check where they lead. If the URL doesn’t align with the organization’s official website, it’s probably a scam.
Watch out for emails that use urgent or threatening language - things like warnings about account suspensions or demands for immediate action are classic phishing tactics. Remember, trustworthy companies will never ask for sensitive information like passwords or financial details via email. When in doubt, reach out to the organization directly through their official website or customer service channels.
Above all, trust your gut. If something feels off, it’s always smarter to double-check than to risk compromising your security.
If you’ve clicked on a phishing link by mistake, don’t panic - but act fast to protect your information. Start by running a full antivirus scan on your device to detect and remove any malware that might have been installed. Next, if you entered any login details after clicking the link, immediately update the passwords for those accounts. Make sure to use strong, unique passwords, and enable two-factor authentication wherever possible for an added layer of security.
Monitor your financial accounts and other sensitive information for any unusual activity. If you spot anything suspicious, report it right away to your bank, email provider, or the affected service. To go a step further, file a report with the Federal Trade Commission (FTC) or other relevant authorities about the phishing attempt. Acting quickly can help limit the damage and safeguard your personal information.
Multi-factor authentication (MFA) strengthens account security by requiring more than just a password to log in. Even if a scammer manages to obtain your password through a phishing email, MFA adds a safeguard: a second verification step. This could be a code sent to your phone or something like biometric authentication, such as a fingerprint.
This extra layer makes it far more challenging for cybercriminals to break in. They'd need not only your password but also access to that second factor, which is typically in your control. By enabling MFA, you drastically lower the chances of falling victim to phishing schemes and help secure both personal and organizational data from unauthorized access.
Compare RSSI, SNR and signal loss to diagnose WiFi issues, optimize access point placement, and reduce interference for stable voice, video, and data.
Learn how to optimize your WiFi settings for video doorbells to ensure seamless streaming and reliable notifications.
Improve your internet speed with practical tips like upgrading your router, managing bandwidth, and securing your network.